TXDNS is a Win32 aggressive multithreaded DNS digger. Capable of placing, on the wire, thousands of DNS queries per minute. TXDNS main goal is to expose a domain namespace trough a number of techniques:
— Typos: Mised, doouble and transposde keystrokes;
— TLD/ccSLD rotation;
— Dictionary attack;
— Full Brute-force attack: alpha, numeric or alphanumeric charsets.
New features:
- Support AAAA(IPv6)record queries:
- Rewrite summarizing statistics using a thread-safe algorithm instead mutex. Read More
November 29, 2012
Short URLHacking Tools, Network Hacking, Network Mapping, penetration testing, Scanners, Security Tools, vulnerability scannerPenetration Testing, Security, Tools

NetSleuth identifies and fingerprints network devices by silent network monitoring or by processing data from PCAP files.
NetSleuth is an opensource network forensics and analysis tool, designed for triage in incident response situations. It can identify and fingerprint network hosts and devices from pcap files captured from Ethernet or WiFi data (from tools like Kismet).
It also includes a live mode, silently identifying hosts and devices without needing to send any packets or put the network adapters into promiscuous mode (“silent portscanning”).
NetSleuth is a free network monitoring, cyber security and network forensics analysis (NFAT) tool that provides the following features:
Read More
November 29, 2012
Short URLForensic Toolkit, Forensics, Hacking Tools, Network Hacking, ScannersHacking, Penetration Testing, Security, Tools
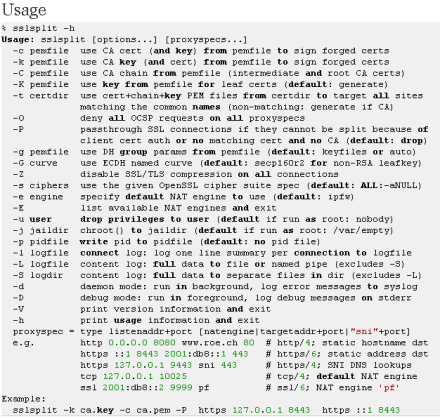
SLsplit is a tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. Connections are transparently intercepted through a network address translation engine and redirected to SSLsplit. SSLsplit terminates SSL/TLS and initiates a new SSL/TLS connection to the original destination address, while logging all data transmitted. SSLsplit is intended to be useful for network forensics and penetration testing.
Change Log:
- Add support for 2048 and 4096 bit Diffie-Hellman
- Fix syslog error messages
- Fix threading issues in daemon mode .
- Fix address family check in netfilter NAT lookup
- Fix build on recent glibc systems
- Minor code and build process improvements
 Read More
Read More
November 29, 2012
Short URLMan-in-the-middle, Network Hacking, penetration testing, Sniffing, spoofing, ssl, VulnerabilitiesPenetration Testing, Security, Tools
A bash script to launch a Soft AP, configurable with a wide variety of attack options. Includes a number of index.html and server php scripts, for sniffing/phishing. Can act as multi-client captive portal using php and iptables. Launches classic exploits such as evil-PDF. De-auth with aireplay, airdrop-ng or MDK3.

Changes and New Features
- “hotspot_3″ is a simple phishing web page, used with basic menu option 4.
- “portal_simple” is a captive portal which allows you to edit the index.html with the name of the portal eg “Joe’s CyberCafe”. It is used for sniffing.
- “portal_hotspot3″ phishes credentials, and then allows clients through the portal to the internet
- “portal_pdf” forces the client to download a malicious pdf in order to pass through the portal
Updated feature list: Read More
November 28, 2012
Short URLHacking Tools, Linux, Network Hacking, Wi-Fi Hacking, wirelessblacktrack, Hacking, Penetration Testing, Security, Tools
Wireshark is the world’s foremost network protocol analyzer, and is the de facto standard across many industries and educational institutions.

• A lot of protocols were updated:
• A bug that caused the HSRP dissector could to go into an infinite loop has been fixed;
• A bug that causeD the PPP dissector to abort has been repaired;
• Martin Wilck discovered an infinite loop in the DRDA dissector. It was fixed;
• HDCP2 now used the correct protocol id;
• Markers are now showed when maps are displayed;
• Truncated/partial JPEG files are now dissected;
• Support for MPLS Packet Loss and Delay Measurement has been implemented;
• A bug that caused Wireshark to crash when VoIP Calls were selected was fixed;
Read More
October 12, 2012
Short URLMonitoring, Network Hacking, Network Mapping, Security Tools, Vulnerability AssessmentGeneral
This module provides security enhancements against (HTTP) Flood & Brute Force Attacks for native PHP or .NET scripts at web application level. Massive crawling/scanning tools, HTTP flood tools can be detected and blocked by this module via htaccess or iptables, etc. You can use this module by including “iosec.php” to any PHP file which wants to be protected.

Features :
This is a unique project and it is the world’s first web application flood guard script.
At web application (scripting) level you can,
– Block proxies. (only via HTTP header)
– Detect flooding IP addresses.
– Slow down or restrict access for automated tools (HTTP flood, brute force tools, vulnerability scanners, etc.)
– Save your server resources (database, cpu, ram, etc.) under an attack.
– Restrict access permanently or temporarily for listed IP addresses in “banlist” file.
– Notify yourself via email alerts when attacks begin.
– Implicit deny for DDoS attacks
October 2, 2012
Short URLCodes, Network Hacking, PHP, Security ToolsPenetration Testing, Security, Tools
Social Engineer Toolkit or SET updated to V4.0 . The latest version code named is “Balls of Steel.” The Social Engineering Toolkit (SET) is an open source, python-driven, social-engineering penetration testing framework of custom tools which solely focuses on attacking the human element of penetration testing.

It was designed in order to arm penetration testers and security researchers with the ability to effectively test heavily advanced social-engineering attacks armed with logical methods. The Social Engineer Toolkit leverages multiple attack vectors that take advantage of the human element of security in an effort to target attackers.
In New version the Java Applet attack has been completely rewritten and obfuscated with added evasion techniques. Additionally, all of the payloads have been heavily encrypted with a number of heavy anti-debugging tools.The powershell attack vectors now support customized payload selection through the config/set_config. A new attack vector has been added called the Dell DRAC Attack Vector (default credential finder).
Read More
September 23, 2012
Short URLExploits, Hacking Tools, Metasploit, MITM, Network Hacking, Network Mapping, penetration testing, Scanners, Security Tools, Social Engineering, Vulnerabilities, Vulnerability Assessment, Wi-Fi Hackingblacktrack, Hacking, Penetration Testing, Security, Tools

Covert VPN is a VPN pivoting technology recently added to CobaltStrike (the commercial Armitage). Once deployed, you have a layer 2 tunnel into your target’s network. This allows you to sniff packets,use external tools, host rogue services, and inject spoofed packets.
To activate Covert VPN, right-click a compromised host, go to Meterpreter -> Pivoting -> Deploy VPN. Select the remote interface you would like Covert VPN to bind to. If no local interface is present, press Add to create one.
Check Clone host MAC address to make your local interface have the same MAC address as the remote interface. It’s safest to leave this option checked.Select Inject VPN client into memory to deploy Covert VPN directly into memory. If this box is not checked, Cobalt Strike will upload and execute the Covert VPN client for you. The inject into memory option does not work reliably on Windows Vista, Windows 7, or 64-bit Windows XP.Press Deploy to start the Covert VPN client on the target. Covert VPN requires SYSTEM access to deploy.
Read More
September 23, 2012
Short URLNetwork Hacking, penetration testing, Vulnerabilities, Vulnerability AssessmentPenetration Testing, Security, Tools
The Network Security Toolkit is bootable ISO live CD/DVD (NST Live) is based on Fedora. The toolkit was designed to provide easy access to best-of-breed Open Source Network Security Applications and should run on most x86/x86_64 platforms.

The main intent of developing this toolkit was to provide the network security administrator with a comprehensive set of Open SourceNetwork Security Tools. An advanced Web User Interface (WUI) is provided for system administration, navigation, automation and configuration of many network and security applications found within the Network Security Toolkit distribution.
In the virtual world, NST can be used as a network security analysis, validation and monitoring tool on enterprise virtual servers hosting virtual machines. Network Security Toolkit also makes an excellent tool to help one with crash recovery troubleshooting scenarios and diagnostics.
Read More
September 23, 2012
Short URLNetwork Hacking, Network Mapping, Security Tools, Vulnerability AssessmentPenetration Testing, Security, Tools